Futuristic view of the Internet of Quantum Drones: Review, challenges and research agenda - ScienceDirect

Futuristic view of the Internet of Quantum Drones: Review, challenges and research agenda - ScienceDirect

PDF) Cryptography Automata Based Key Generation | IJSR in Network Security and Communication (IJSRNSC) - Academia.edu

Decentralized Service Protocol, Automata Network, Launches a Solution for the Miner Extractable Value (MEV) Issue | Coinspeaker
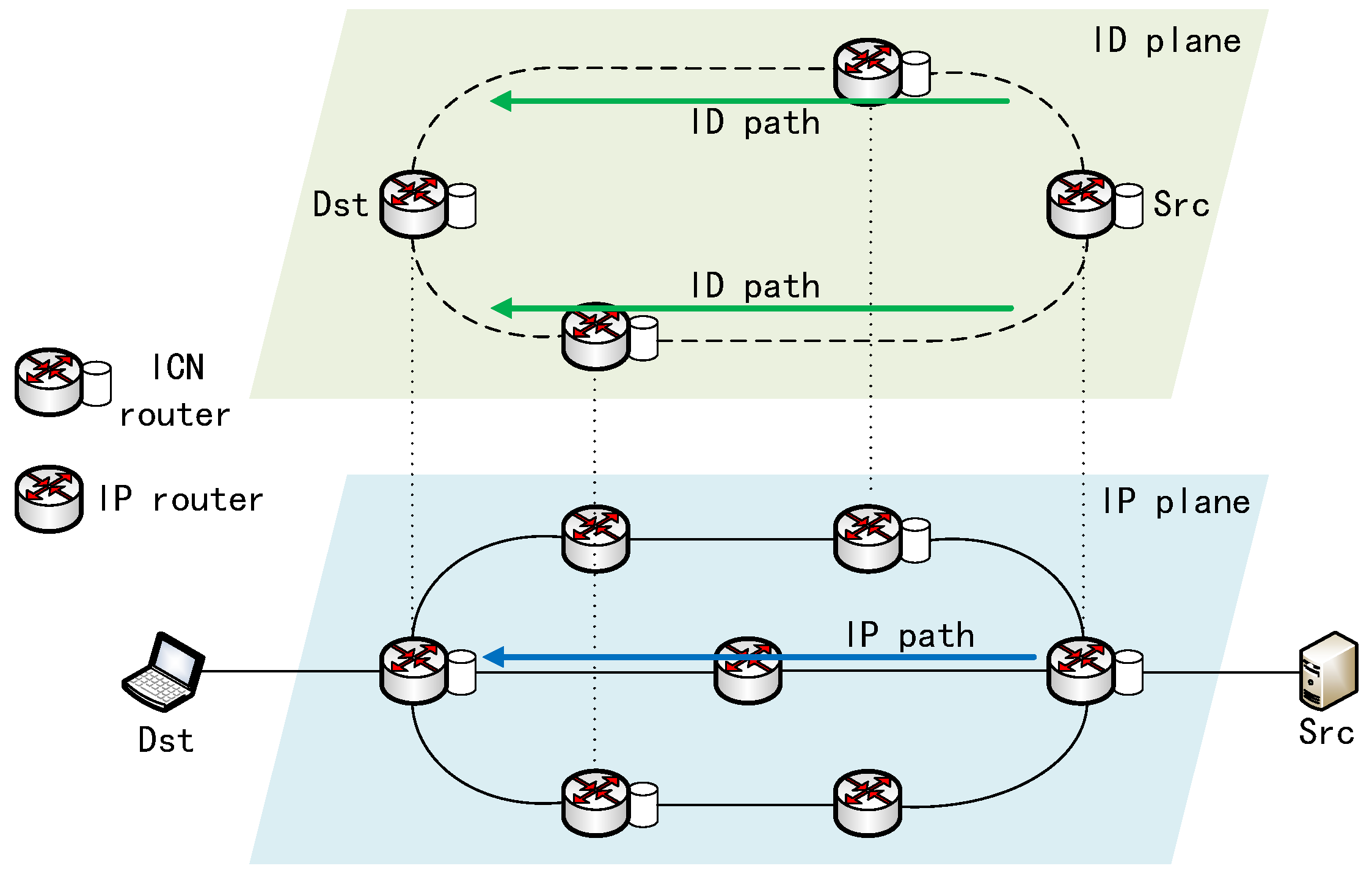
Future Internet | Free Full-Text | A Multipath Data-Scheduling Strategy Based on Path Correlation for Information-Centric Networking

An Approach to Cryptography Based on Continuous-Variable Quantum Neural Network | Scientific Reports
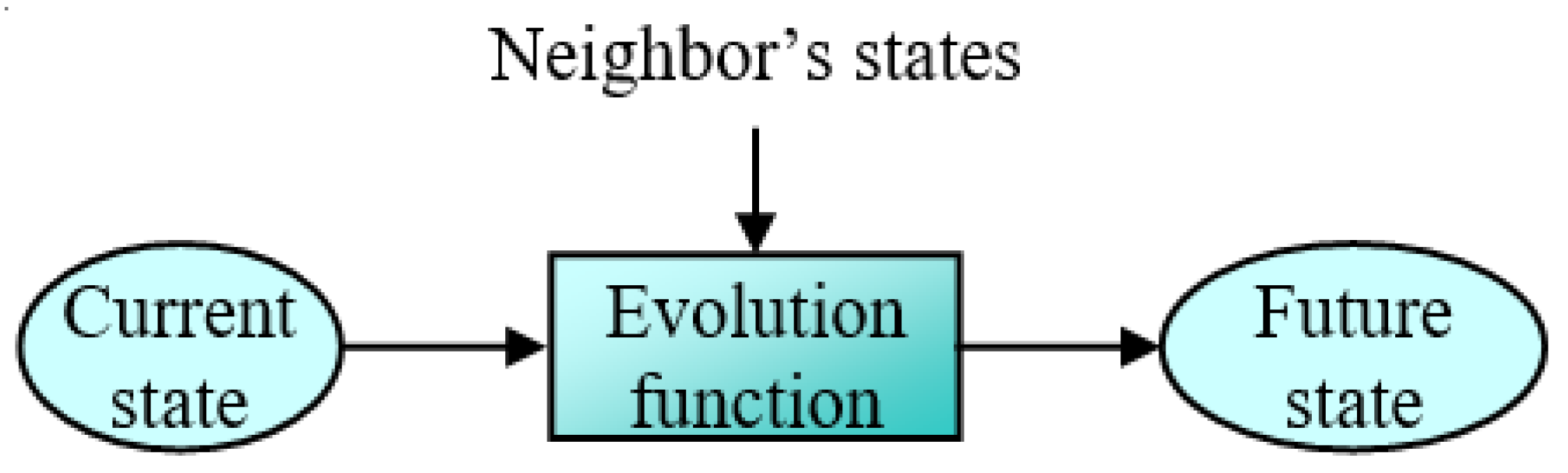
PDF) Novel and Efficient Cellular Automata Based Symmetric Key Encryption Algorithm for Wireless Sensor Networks
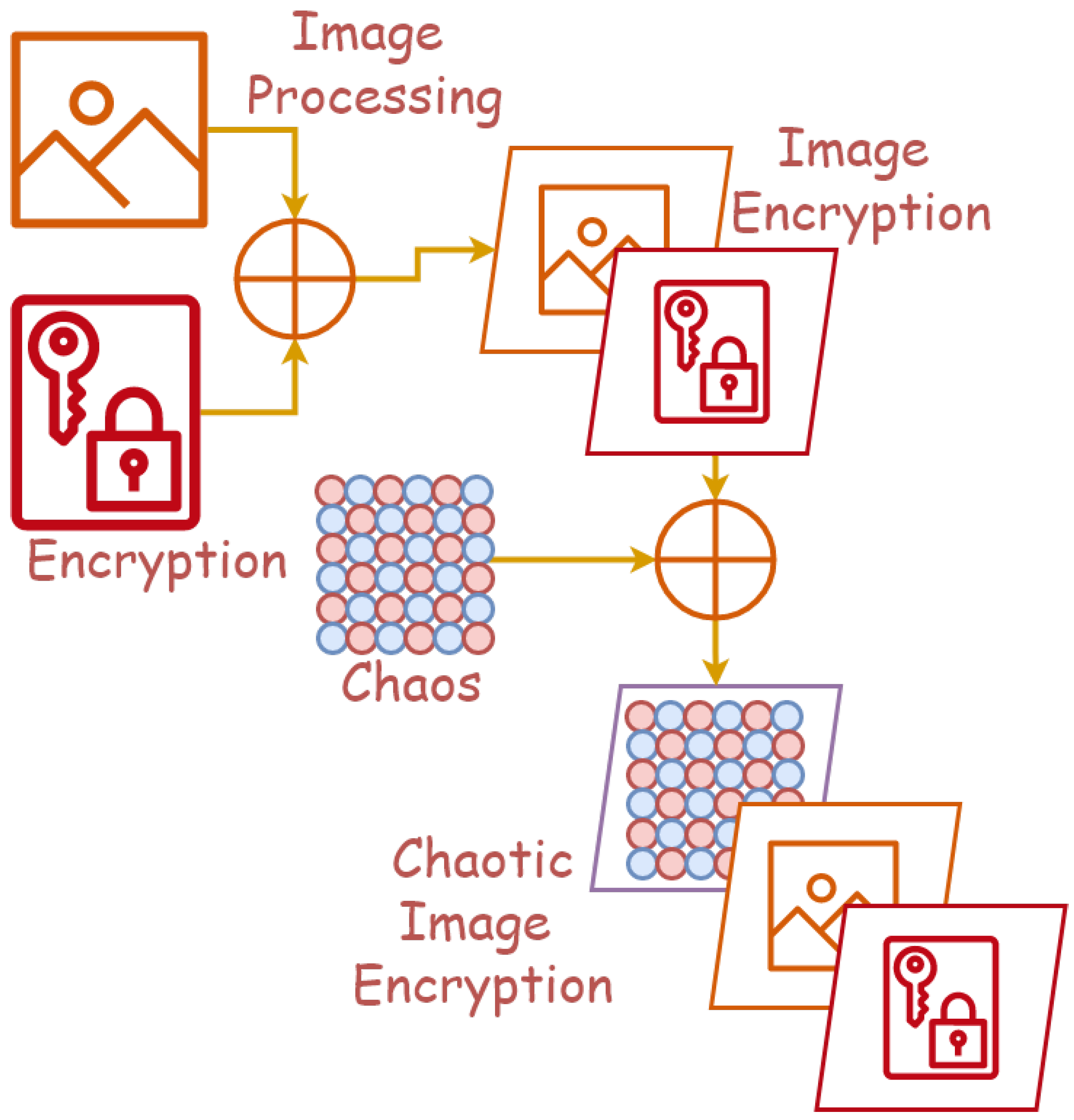
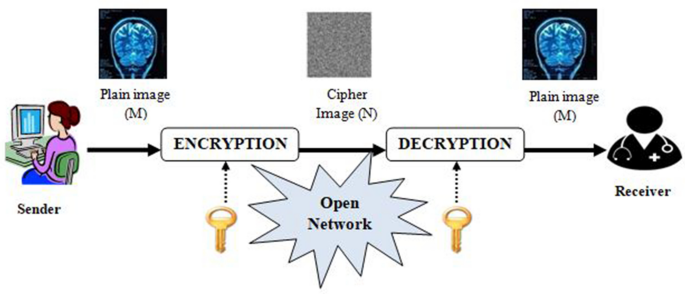
Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains | SpringerLink



![Top 5 Latest Computer Network Research Topics [Research Guidance] Top 5 Latest Computer Network Research Topics [Research Guidance]](https://phdservices.org/wp-content/uploads/2021/08/Research-Computer-Network-Projects-With-Source-Code.jpg)