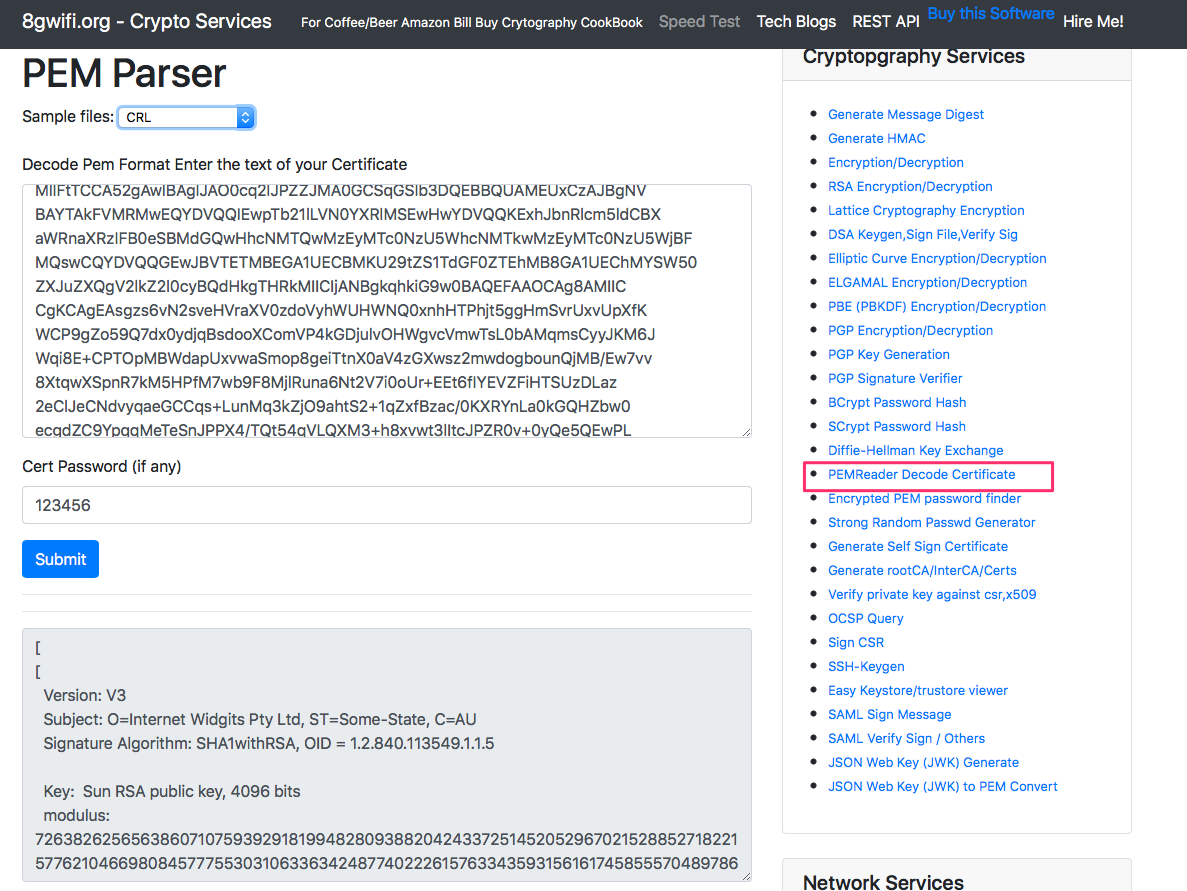
Automatically block suspicious traffic with AWS Network Firewall and Amazon GuardDuty | AWS Security Blog

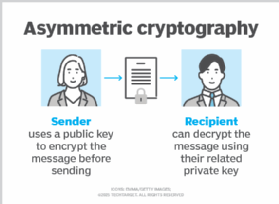
SSH keys authenticate users and hosts in SSH. They are used for single sign-on and machine-to-machine access. Security and convenience!