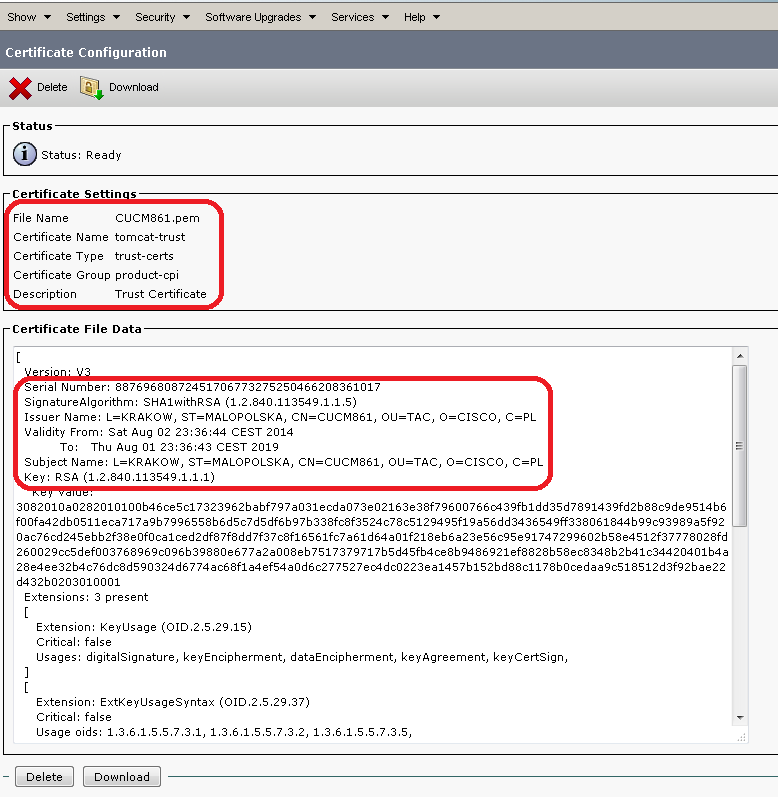
BusinessObjects BI Platform 4.1 – Setting up an SSO connection to SAP HANA to utilize in Design Studio 1.1 | SAP Blogs

BusinessObjects BI Platform 4.1 – Setting up an SSO connection to SAP HANA to utilize in Design Studio 1.1 | SAP Blogs

BusinessObjects BI Platform 4.1 – Setting up an SSO connection to SAP HANA to utilize in Design Studio 1.1 | SAP Blogs

Integrating 3rd-party Cryptographic Providers into NetWeaver Java – What's Possible and What's Not | SAP Blogs

BusinessObjects BI Platform 4.1 – Setting up an SSO connection to SAP HANA to utilize in Design Studio 1.1 | SAP Blogs

Integrating 3rd-party Cryptographic Providers into NetWeaver Java – What's Possible and What's Not | SAP Blogs

Integrating 3rd-party Cryptographic Providers into NetWeaver Java – What's Possible and What's Not | SAP Blogs