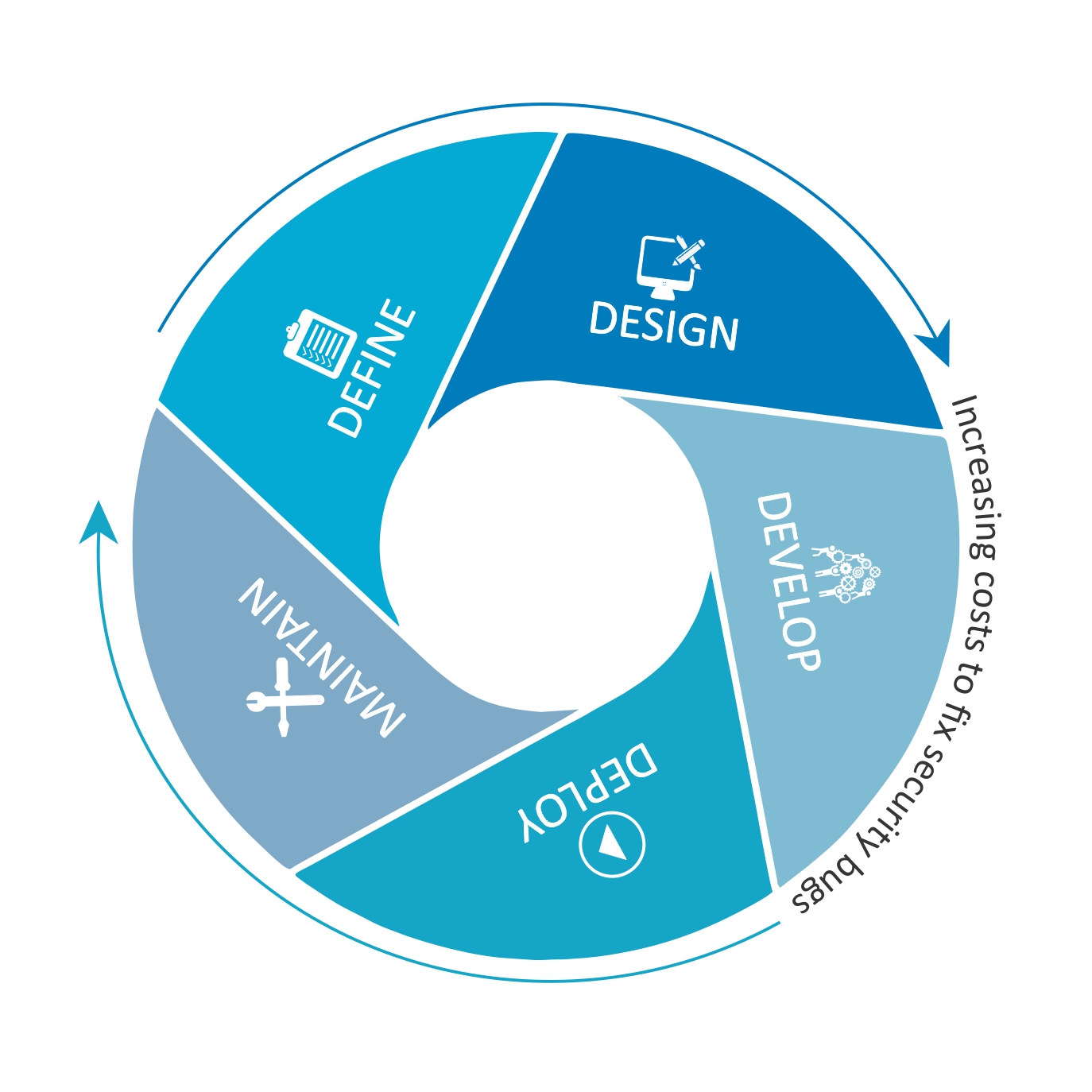
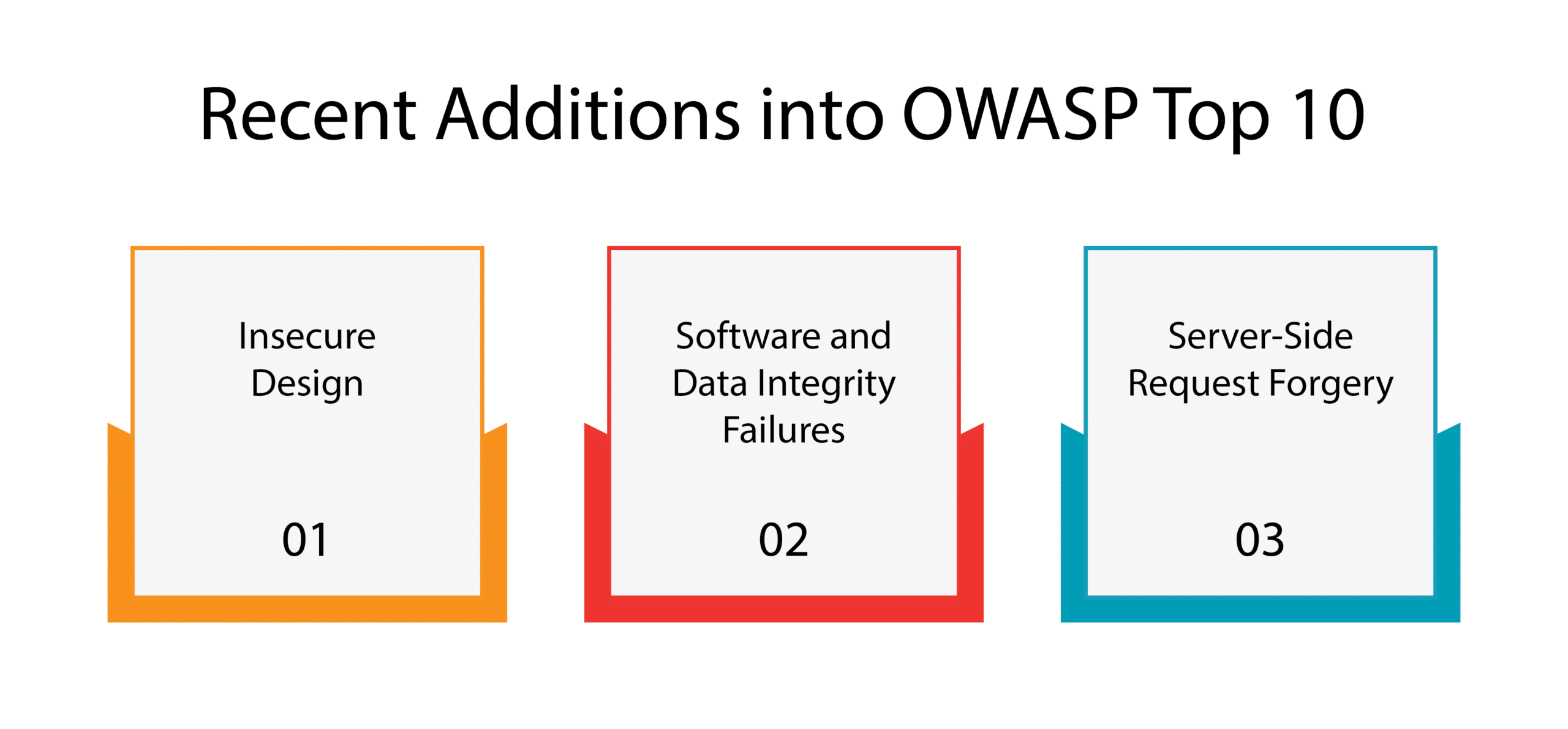
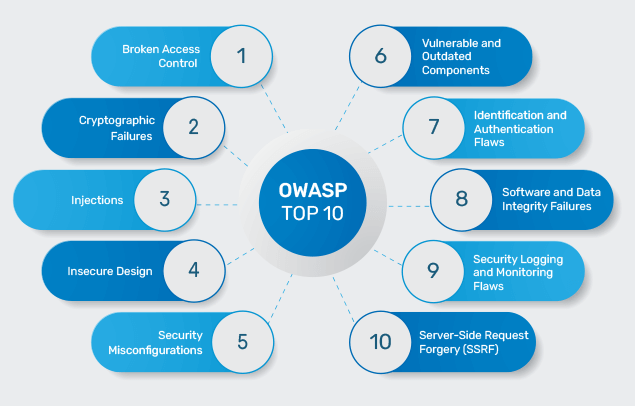
GitHub - OWASP/Nettacker: Automated Penetration Testing Framework - Open-Source Vulnerability Scanner - Vulnerability Management
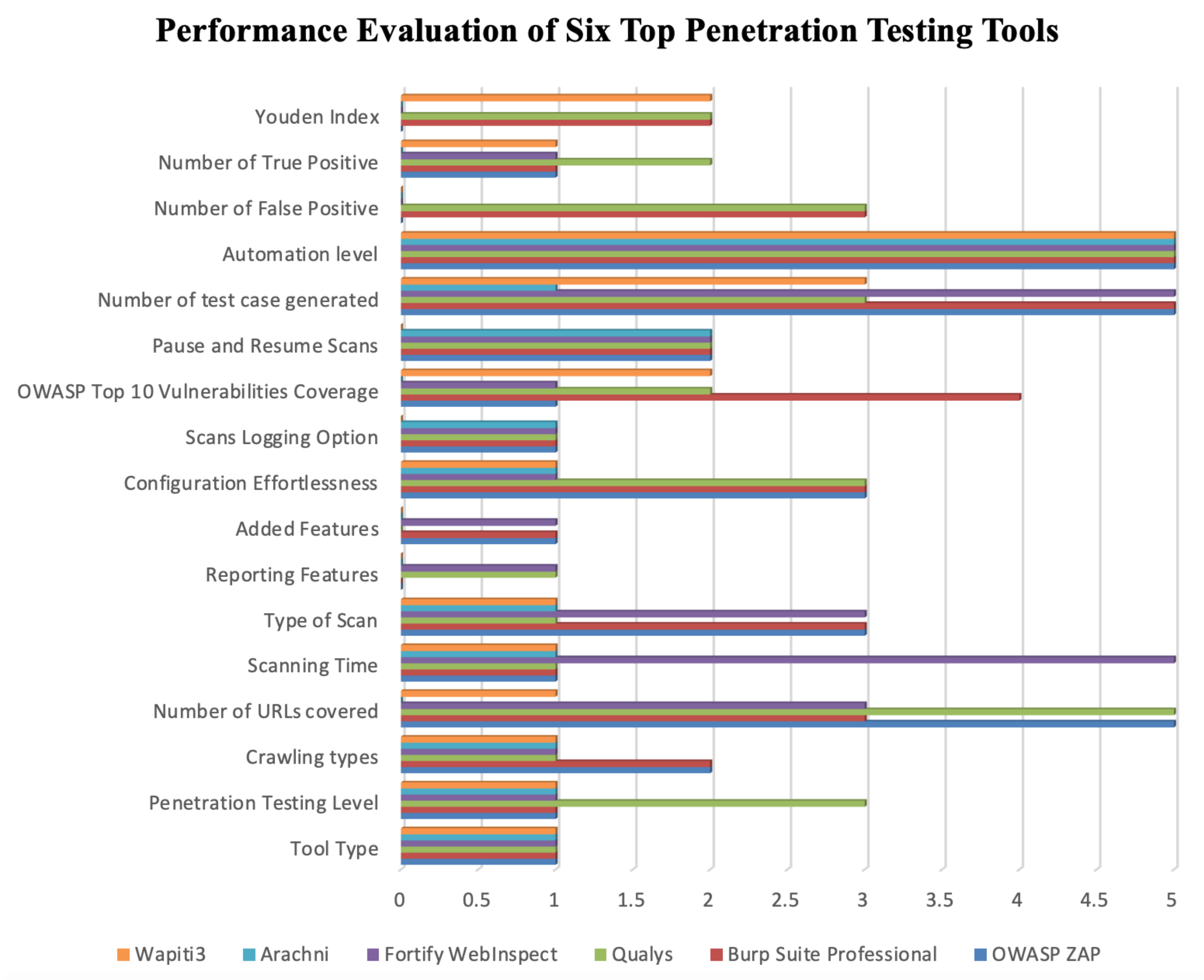
Electronics | Free Full-Text | An Empirical Comparison of Pen-Testing Tools for Detecting Web App Vulnerabilities

Performing a Pen Test after each Deployment using OWASP ZAP, Azure Container Instances, and Azure DevOps
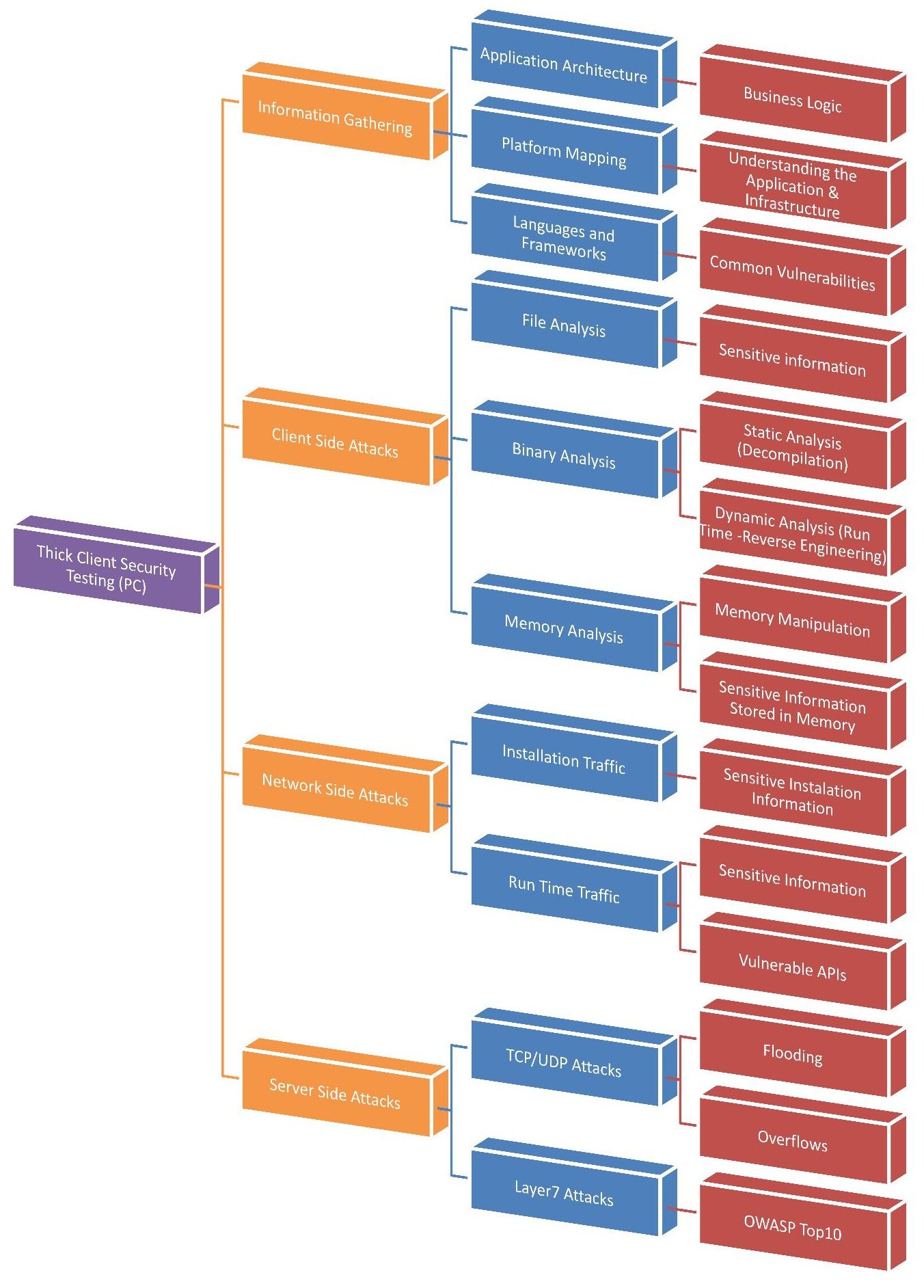
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/4-Table1-1.png)