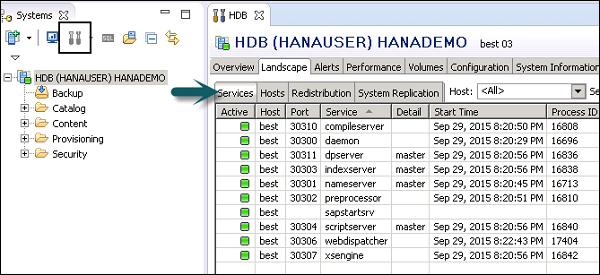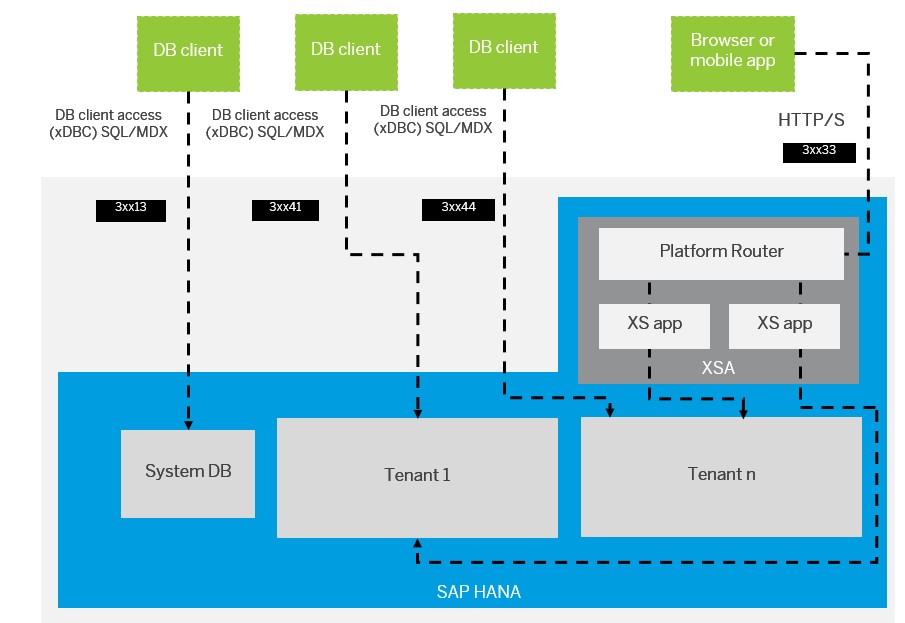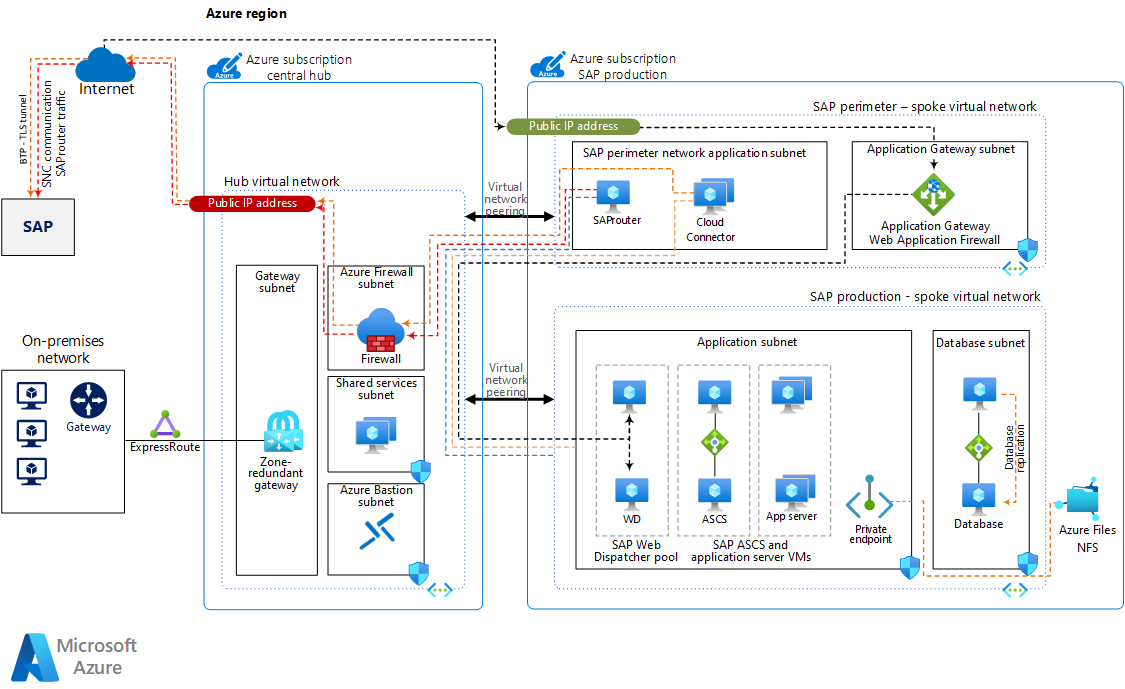
Inbound and outbound internet connections for SAP on Azure - Azure Architecture Center | Microsoft Learn

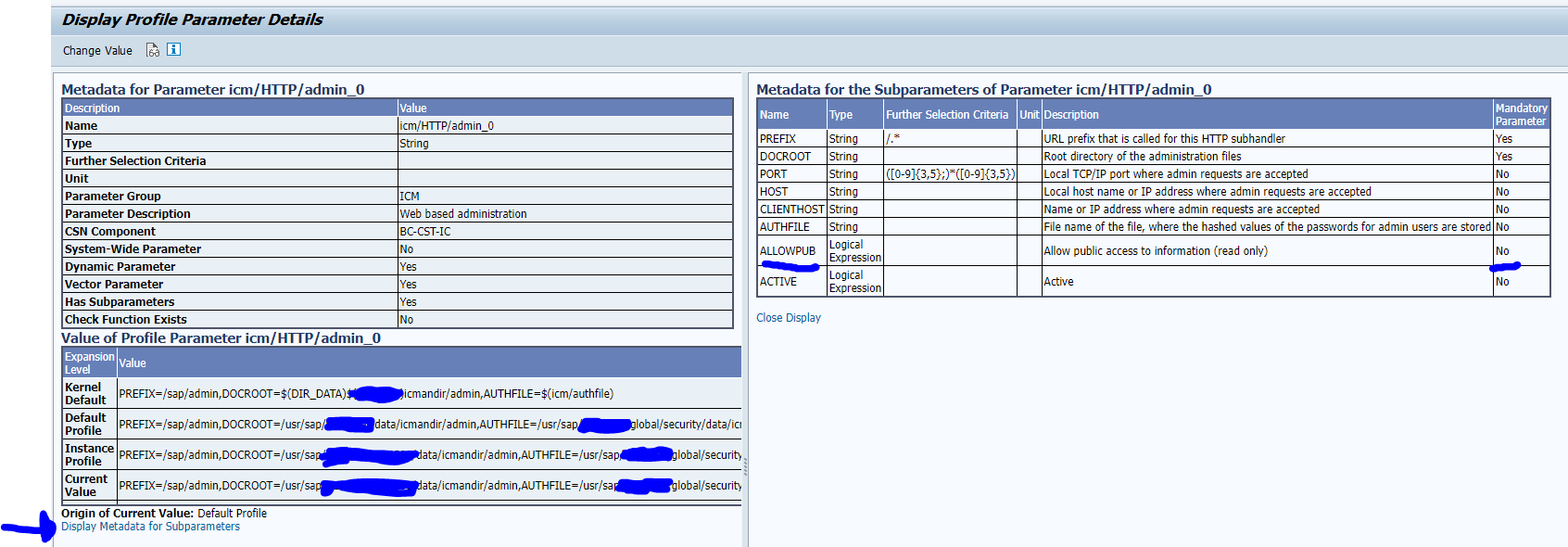
SUSE Linux Enterprise Server for SAP Applications 15 GA and SP1 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 15 GA and SP1