Comparison of the TCP and SSH handshakes in direct connection and via... | Download Scientific Diagram

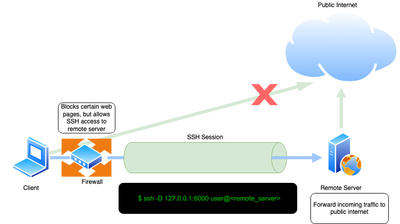
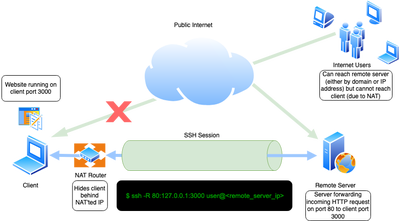
Bypass Filtering Systems on Pcs Without the Insecurities of TOR (the Onion Router) or Tunneling Internet Over SSH : 5 Steps - Instructables
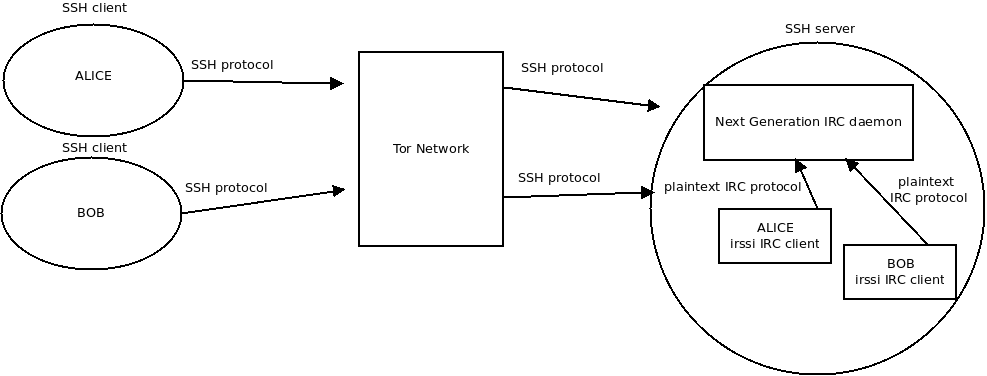
GitHub - banditopazzo/torssh: A simple utility to use SSH and SCP over Tor. Includes a "universal" wrapper to proxy your applications over Tor