Hacking the Code: Auditor's Guide to Writing Secure Code for the Web: Burnett, Mark: 9781932266658: Amazon.com: Books
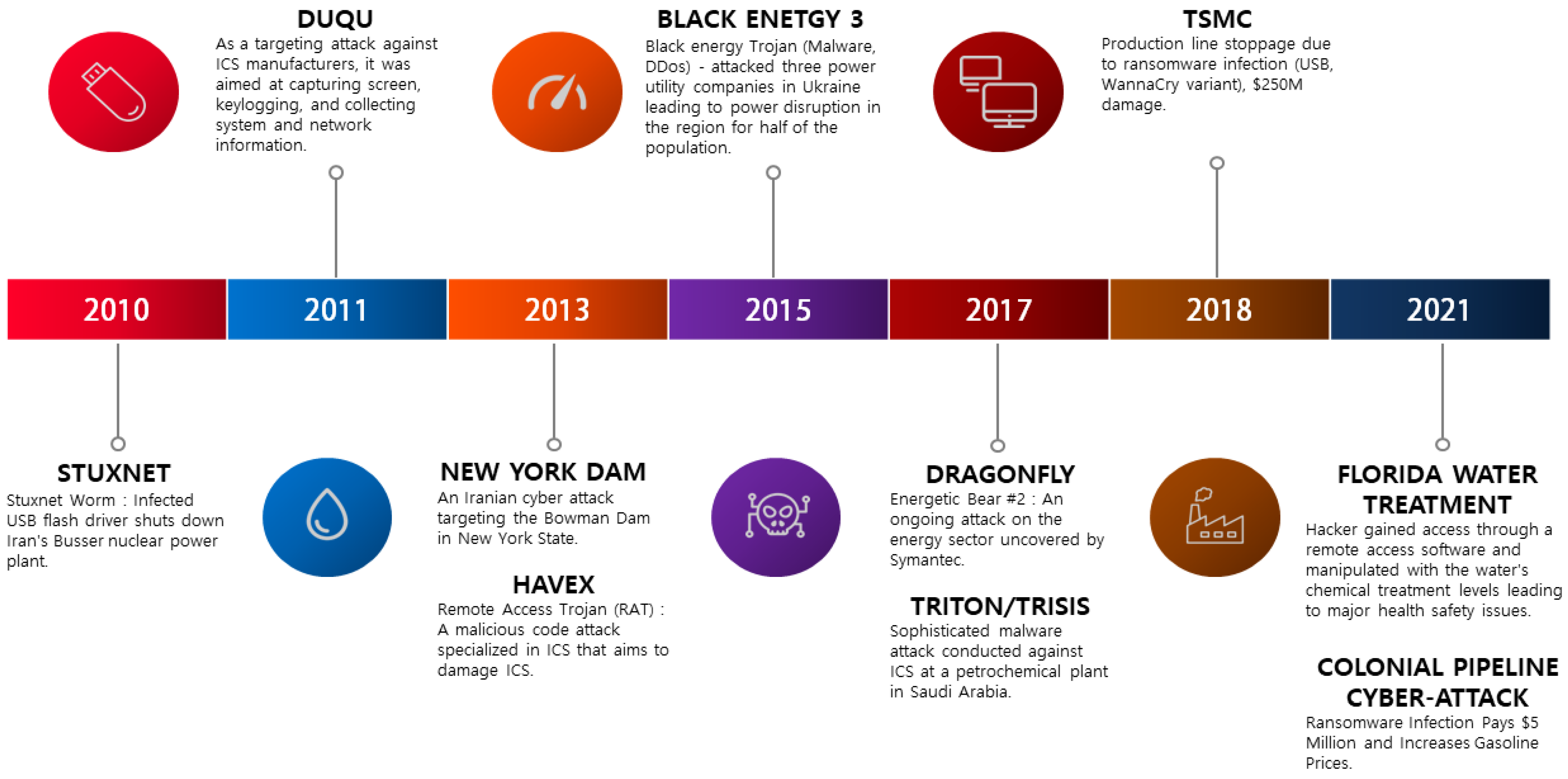
Applied Sciences | Free Full-Text | IIoT Malware Detection Using Edge Computing and Deep Learning for Cybersecurity in Smart Factories
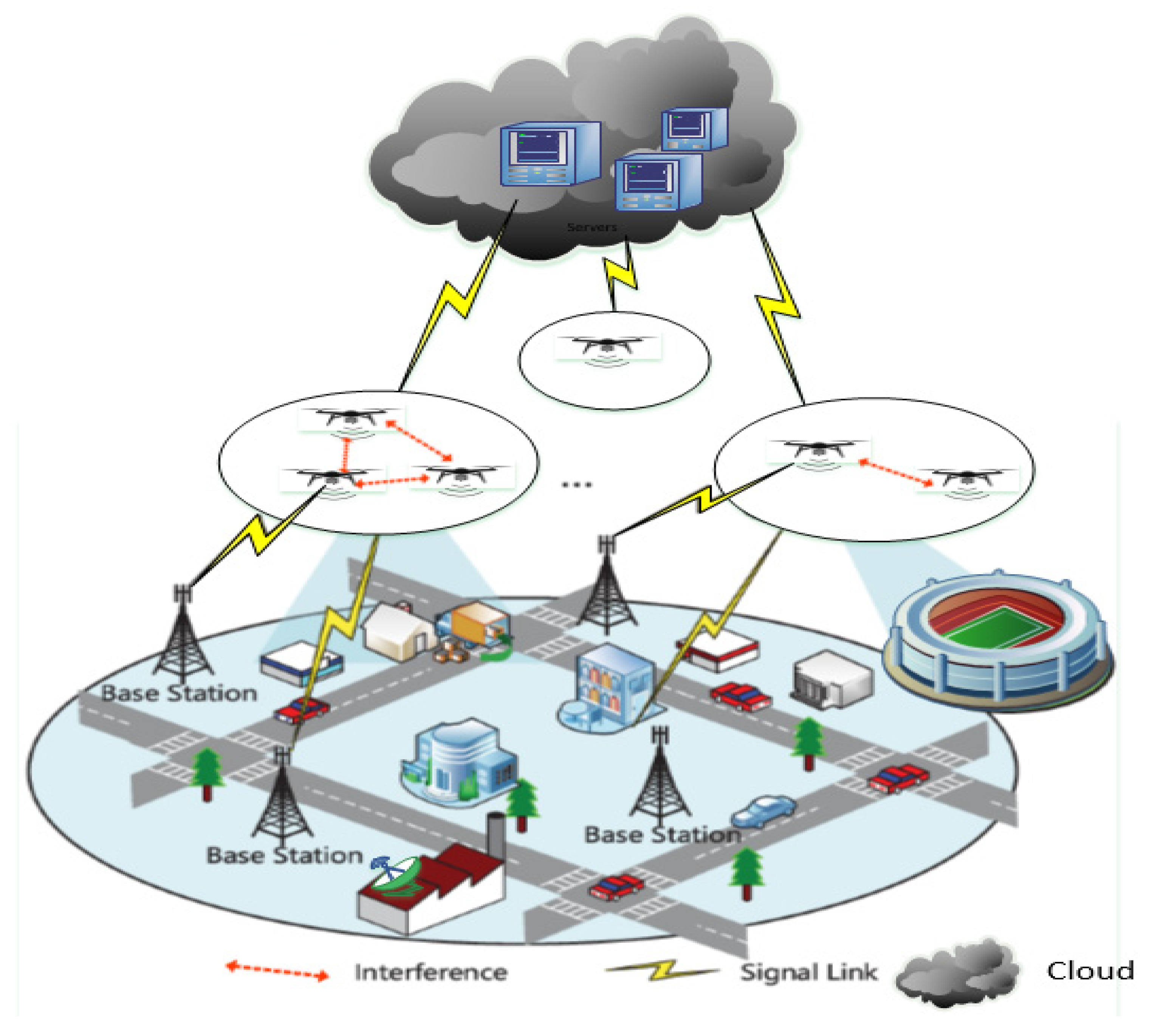
Sensors | Free Full-Text | The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends

Hacking the Code: Auditor's Guide to Writing Secure Code for the Web: Burnett, Mark: 9781932266658: Amazon.com: Books